Honey Potting suite
Echo:
Advanced Cybersecurity Solution
Internal network telemetry, creating fake server targets, and recording attackers’ movements within the network for actionable threat intelligence.
Witness real-time incoming attacks on your network
Attack Vector Detection
See the attack vectors towards a specific production infrastructure, network, or application.
Threat Intelligence
Identify the location and origins of your attackers. Discover the specific regions that are attacking your infrastructure the most.
Vulnerability Identification
The honeypot system helps identify CVE that hackers are attempting to exploit.
Leading Non-invasive Threat Visualization
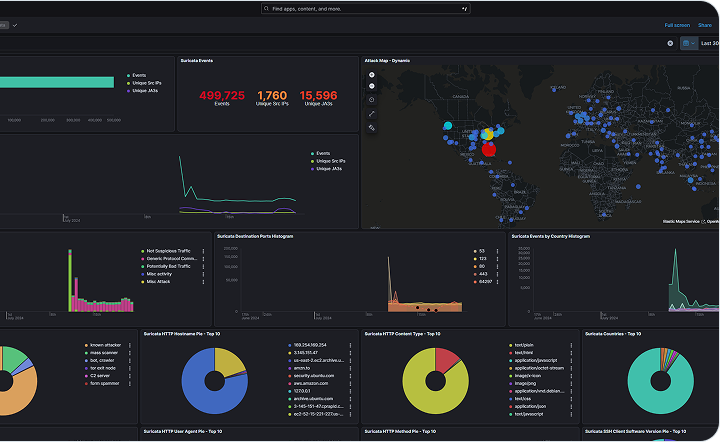
Review Attacks Over Any Past Timeframe
Understanding historical attack patterns will help identify vulnerabilities and strengthen your defenses. Review comprehensive reports that provide a clear picture of your security landscape over any time period.
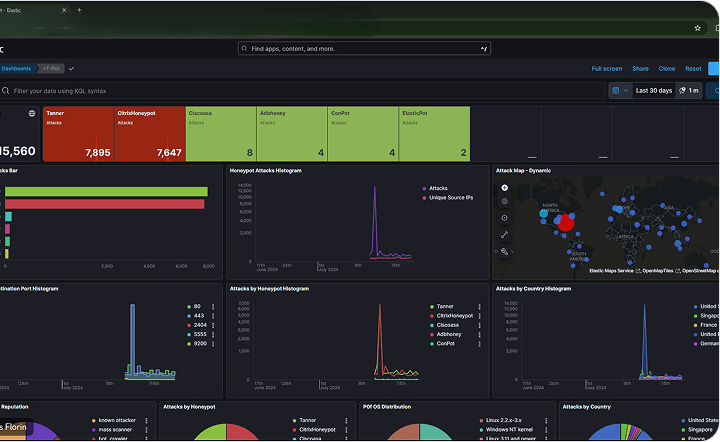
Review All Attack Targets
Discover which ports, files, and systems are most frequently targeted by cyberattacks with our detailed reports. By understanding the specific entry points and assets at risk, you can strategically fortify your defenses and protect the most vulnerable areas of your infrastructure.
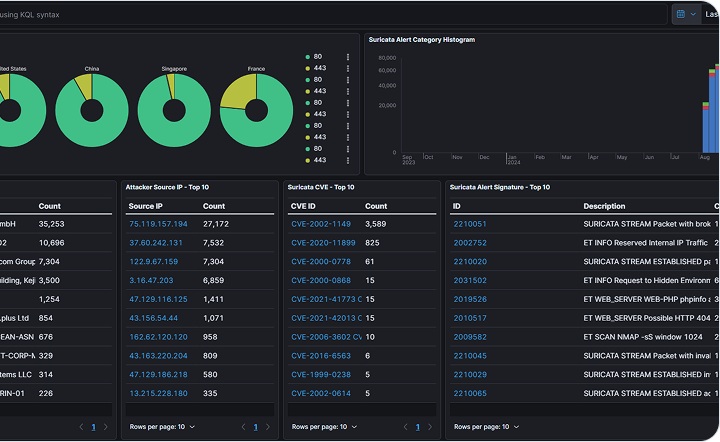
Honeypot Attack Sources/CVEs
The "Sources and CVE" visualization showcases the origins of attacks captured by the honeypot, along with the specific vulnerabilities (CVE) exploited.
This detailed representation allows for a clear understanding of the attack sources and the vulnerabilities targeted, providing essential insights for fortifying defenses and addressing critical security gaps.
This detailed representation allows for a clear understanding of the attack sources and the vulnerabilities targeted, providing essential insights for fortifying defenses and addressing critical security gaps.
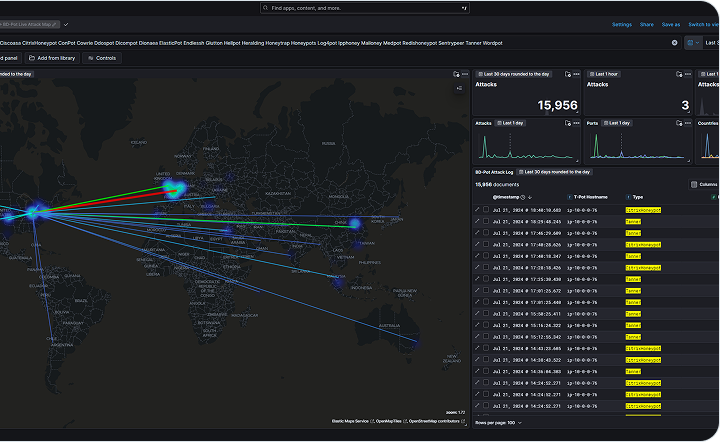
Live Attack Surfaces
The "Live Attack Surfaces" map provides a real-time visualization of ongoing cyber threats, highlighting where potential attackers are attempting to breach your systems.
This dynamic tool offers an immediate view of the attack landscape, enabling rapid identification and response to emerging threats, ultimately enhancing your organization's security posture.
This dynamic tool offers an immediate view of the attack landscape, enabling rapid identification and response to emerging threats, ultimately enhancing your organization's security posture.
How can these best work in your firm?
Work with our team to see how these tools can boost your firm’s security and performance. Don’t wait—unlock actionable insights and drive results

